· Mohamed-Hacène Boukerma · Articles · 5 min read
Security Orchestration, Automation, and Response (SOAR)
This article is an introduction to Security Orchestration, Automation, and Response

This article is an introduction to Security Orchestration, Automation, and Response. Indeed, it aims to present and popularize this system, becoming increasingly topical.
I. Context
Let’s give some context before starting to go deeper in this topic. SOC (Security Operation Center) is a team (internal or external to the company) composed by Cybersecurity professionals, monitoring the entire IT infrastructure 24/7. They have different tools to help them identify and register threats to improve the security system like SIEM (Security Information and Event Management) or EDR (Endpoint Detection and Response). Some of you will also be familiar with XDRs (Extended Detection and Response), which are simply an extension of the EDR’s range of action. While EDR is monitoring and securing terminals to identify suspicious activities and potential security breaches at the endpoint level, SIEM is collecting, analyzing and stocking a huge amount of data but remains passive in the incident response.
EDR vs SIEM
Endpoint Detection and Response (EDR):
- Focuses on monitoring and securing endpoints like desktops, laptops, servers, and mobile devices.
- Utilizes advanced threat detection techniques such as behavioral analysis and machine learning algorithms.
- Provides granular visibility and control at the endpoint level.
- Helps identify suspicious activities and potential security breaches.
- Enables swift incident response at the endpoint level.
Security Information and Event Management (SIEM):
- Aggregates and analyzes security data from various sources across the network, including logs, network traffic, and system events.
- Offers comprehensive visibility into an organization’s security posture.
- Facilitates real-time threat detection, incident response, and compliance management.
- Provides centralized monitoring and analysis of security events and incidents.
- Supports a wide array of security data sources for holistic threat detection and management.
Differences
- EDR focuses on endpoint-specific threats and responses, while SIEM encompasses a broader range of security data sources.
- EDR provides granular visibility and control at the endpoint level, whereas SIEM offers centralized monitoring and analysis across the entire IT infrastructure.
Common Points
- Both EDR and SIEM aim to enhance security posture, detect threats, and enable swift incident response.
- They play complementary roles in a cybersecurity framework, with EDR focusing on endpoint security and SIEM providing broader visibility and analysis capabilities across the network.
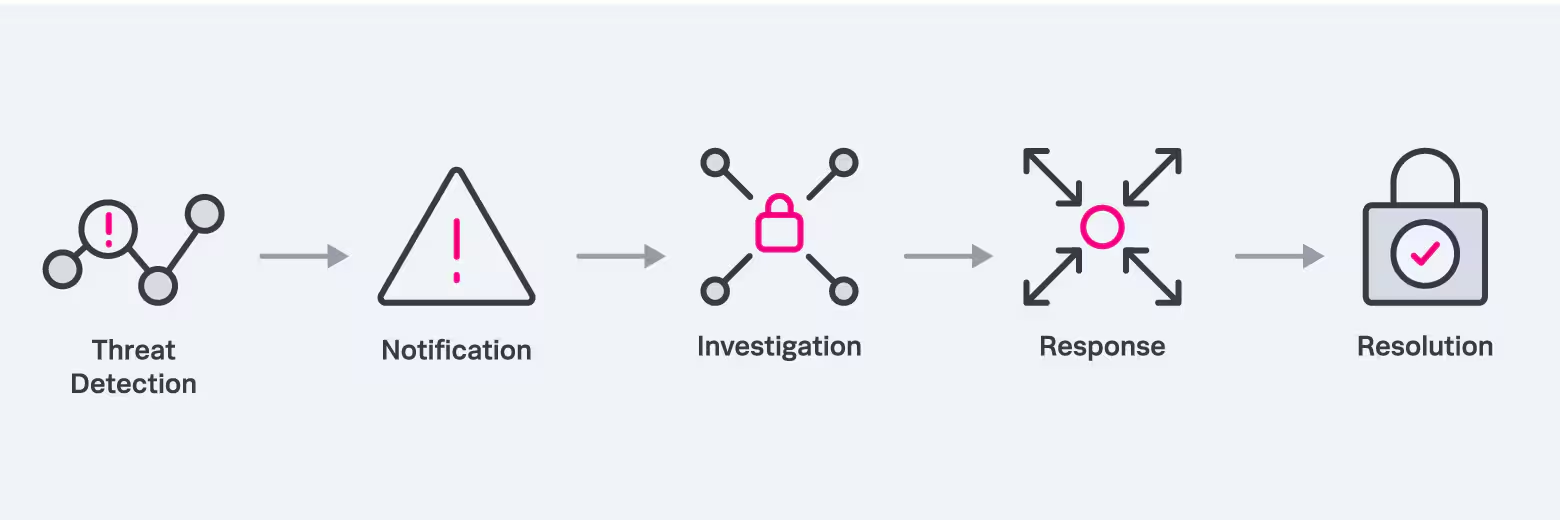
Now, SOAR can literally associate and orchestrate these tools to assist the analyst since the threat detection from various sources to the automated response or report. It can even make decisions on simple incidents that don’t require the intervention of an analyst to resolve them. It’s organized inside a workflow (also known as playbook) where you link all softwares with their APIs, in a precise order, like an analyst would do. At the end you save a lot of time and repetitive effort to concentrate on problems requiring human creativity and intuition.
SOAR basic workflow
So a natural question is, why isn’t everyone using a SOAR today? Actually, this solution is quite complex and expensive because you need a mature team working on it everyday to create new workflows, parse API returns to adapt tools with each other and of course the maintenance of all these workflows. Moreover, to get the most out of it, you need to combine it with a SIEM. This is why XDR is known as a good option for companies not wishing to spend as much because it offers advanced detection, rapid response, and intuitive automation. Obviously, you will not get the same liberty and level of automation and response but it is a serious alternative.
II. Workflow
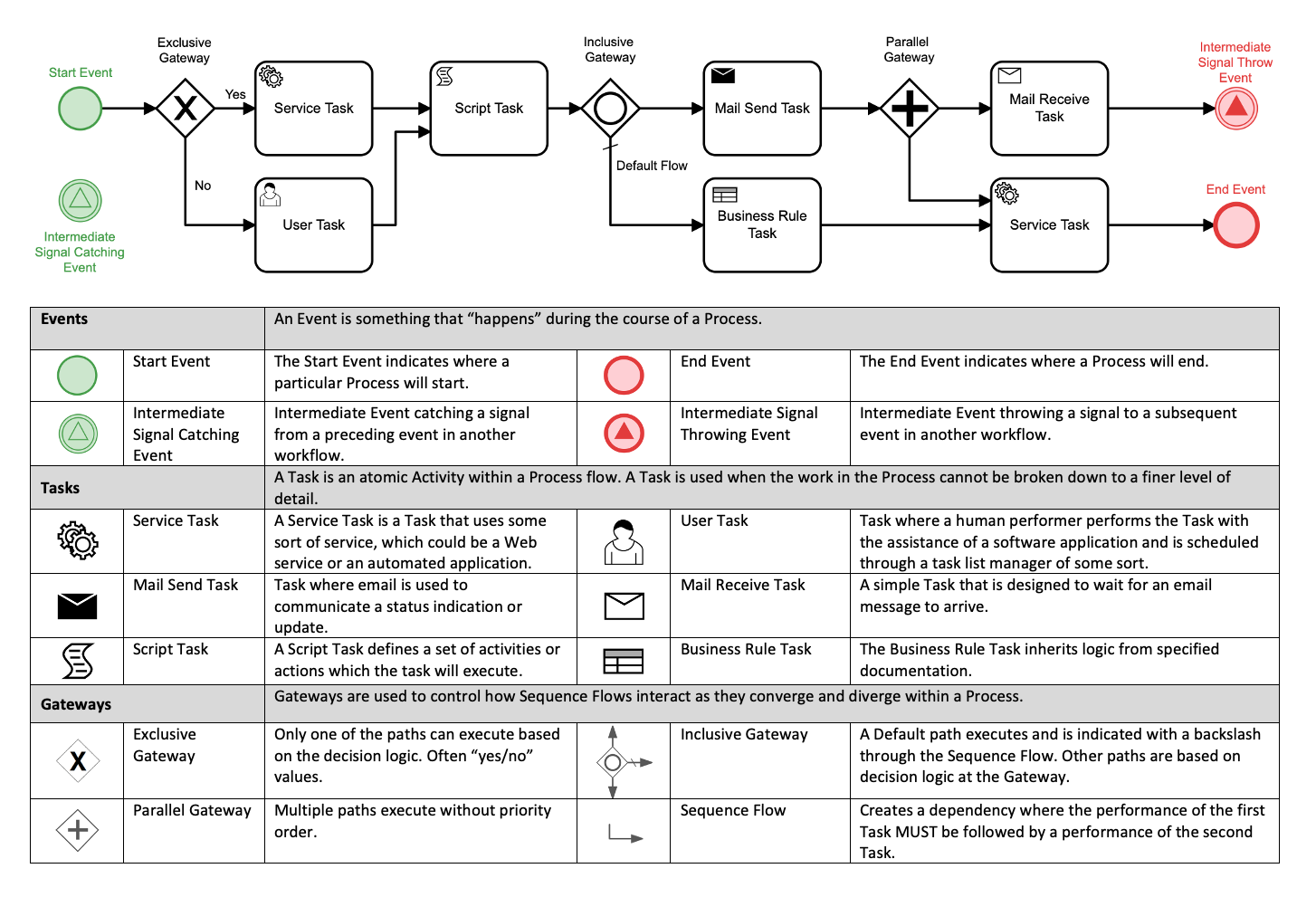
Workflows are at the core of SOAR. This is where all the tools come together and decisions are made. Their basic design is quite simple: A given event (webhook or API call from a third-party application) triggers a certain number of cascading actions to respond to the recorded incident. Sometimes, the workflow will pause waiting for a human decision in specific cases where the answer requires further thought across Jira or by mail for example. At the end, we have precise action in the incident response process according to what path the process followed or a trigger to start another workflow. So, we can naturally interweave workflows, this improves overall SOAR hygiene and maintenance, as they are more precise and less bulky. Here is a flow chart from a Github repository that clearly illustrates the organization of a workflow:
There are a number of open-source Orchestrators you can use if you’re interested in this subject, but the next step is to create your first workflow to discover the difficulties and benefits for yourself.
III. Use cases and benefits
In conclusion, Security Orchestration, Automation, and Response (SOAR) platforms offer a multitude of benefits and use cases that are invaluable in today’s cybersecurity landscape. With features like incident response automation, SOAR platforms empower security teams to stay ahead of cyber threats and effectively manage security incidents. As organizations continue to face evolving cyber threats, adopting SOAR platforms becomes increasingly essential to ensure proactive and effective cybersecurity defenses. Here are just a few of the benefits and common use cases that may apply to you, so feel free to explore all it can do.
Benefits
- Improved Efficiency: Automation reduces manual effort, enhancing productivity.
- Rapid Response: Enables quick response to security incidents, minimizing potential damage.
- Centralized Visibility: Provides a single platform for monitoring and managing security incidents, enhancing situational awareness.
Use Cases
- Incident Response Automation: Automates the entire incident response process, from alert triage to remediation.
- Threat Hunting: Automates threat detection and analysis to identify potential security threats proactively.
- Combatting cyberattacks : Detect and response to phishing, malware and other attacks, minimizing the impact on users and systems.